
The legendary KringleCon CTF is an event that takes place every year with the help of sponsors like SANS, google and others. This year, despite having little time in my schedule, I decided to participate. I managed to solve half of the challenges offered by the competition and it was certainly an incredible experience that I would like to repeat next year.
CTF Context
Under the context of a cybersecurity attack targeting the North Pole, cibersecurity defenders has been entrusted with the mission of solving different practical challenges to save Christmas, using all his cibersec knowledge.
After creating an in-game avatar, we can navigate through a map full of secrets, talking to different NPCs who will give us clues and assign challenges to solve. Undoubtedly, this CTF concept (which has a great resemblance to Jeopardy) is a beautiful representation of a game that I would like to repeat in the following years. You can chat with other players in a chat panel on the right of the screen and also view conference chats from within the game.

Speaking of the challenges themselves: the game consisted of rescuing 5 rings lost in the caverns of the North Pole, where for each ring we will have to solve a series of challenges from different categories such as web, cloud, threat hunting, forensics, priv. climbs etc.
In the following section I'll show you 2 reviews of the most fun challenges I was able to complete that I documented in the final competition report.
Elfen ring: Jolly CI/CD

After speaking with Tinsel Upatree (NPC), the CI/CD mission was requested as the final challenge to retrieve the Elfen Ring. The terminal reveals some notes about this last test.

As the statement reports a web store and since the machine has nmap installed, a small reconnaissance of the IP segment (where the host machine lives) to find exposed web services was started.

From here it was discovered that the IP 172.18.0.150 has a web server, so the content of the web page was requested using the curl tool.

The discovered page maintains a gitlab server in production, which is an interesting point to review, since the challenge speaks precisely of "Continuous Integration and Continuous Deployment", which is the use given to gitlab.
Using the gitlab API, it was possible to find an interesting public project called «Wordpress.flag.net.internal.git» from «rings-of-powder»

After that, using the «git clone» command, the repository is downloaded to the local machine.

From here, the directory tree and other types of files in the repository were reviewed, finding sensitive information such as credentials, but nothing that could be useful, therefore, the different developer commits were checked, in order to find sensitive information leaked from the production environment.
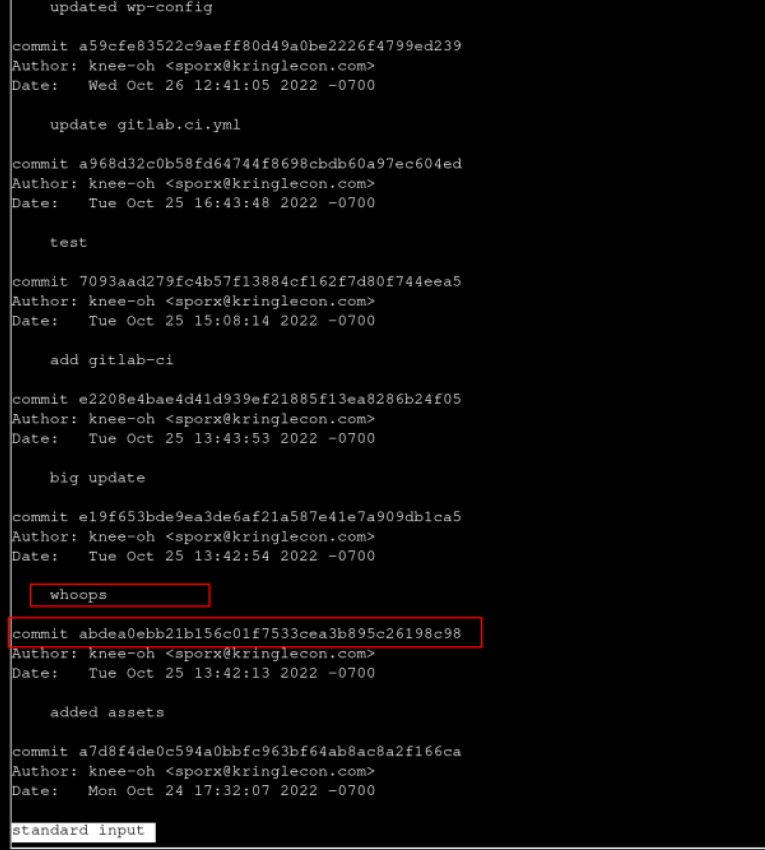
In the commit «abdea0ebb21b156c01f7533cea3b895c26198c98», it was noticed that a comment “woops” was pushed, so it was reviewed the corrections made by the developers that allow to find a private SSH key committed.

Also, note that there is a user named sporx@kringlecon.com who is the author of the commits.
Several attempts to connect to the host were made with the SSH key, but all were rejected. It was devised to use this key to upload a malicious file to the WordPress webhost, in order to obtain a small WebShell for remote code execution.
First, an SSH config. file was configured to use the found private SSH key (now stored in a file called key.pem).

After that a simple webshell was created to execute commands. Since WordPress uses PHP as its backend, a file named “error.php” was created and the malicious code to execute the commands was written there.

This file was placed in the WordPress root path and the changes were pushed to the repository.

Some simple commands were tried to verify that the webshell works and...

nice!. Finally, the flag is listed in the «/» directory of the server and printed using the «cat /flag.txt» command.

Thanks to Fjv for the help in this challenge ;)
Tolkien Ring: Windows Event Logs
Challenge file:

This challenge consisted of solving 10 questions related to a Windows EVTX log file, which detailed most of the commands executed by the attacker on the compromised machine (something we don't see every day).
In order to solve this challenge, we downloaded the powershell.evtx file and start a little recognition of the timestamps, users, and other important information. Also, note that I am using EVENT LOG EXPLORER, a very usefull tool to analyze evtx files. (see my post Something about win Artifacts to know more about this tool)

1. What month/day/year did the attack take place? for example, 09/05/2021
As we see in the last image, most of the log activity is performed on the date 12/24/2022 (dd/mm/yyyy format).
2. An attacker got a secret from a file. What was the original file's name?
After sorting the log table using time field, it was possible to see that at approximately 8:00 UTC -00 a.m. on December 24, the user Chris Massey made his first suspicious movements inside the machine.

How do I really know that these movements are suspicious? Because if we look at the older log entries, the user never performs any concrete action using PowerShell, so the behavior of the user to open a file using the terminal is not an action that would normally do. In fact, older PowerShell log entries only show information from automated scripts, which we assume is legitimate behavior.

In the last image, we can see that the attacker tries to retrieve the content of the Recipe file using the "Get-Content" command. The original file name in this case was Recipe.
3. The content of the previous file were retrieved, changed and stored to a variable by the attacker. This was done multiple times. Submit the last full powershell line that performed only these actions.
If we manually inspect the next log entries, we will eventually see a command where the attacker performs some interesting actions.
Command:
$foo = Get-Content .\Recipe| % {$_ -replace 'honey', 'fish oil'} $foo | Add-Content -Path 'recipe_updated.txt'
In the first part of the command, the attacker assigns the entrie content of the «.\recipe» file to a $foo variable. After that, it tries to replace the string 'honey' with 'fish oil' and finally stores the modified content of the recipe in the recipe_updated.txt file.

4. After storing the altered file contents into the variable, the attacker used the variable to run a separate command that wrote the modified data to a file. This was done multiple times. Submit the last full PowerShell line that performed only this action.
If we continue scrolling through the logs that occurred between 8:06 and 8:03 a.m., we will see that the attacker adds the contents of the $Foo variable multiple times in files with the name "recipe".

Using the string "foo", it was possible to filter all the commands that use this variable, making it much easier to find the answer to this question.
Command:
$foo | Add-Content -Path 'Recipe.txt'5. The Attacker ran the previous command against a file multiple time. What is the name of this file?
As we see in the previous image, the file name is recipe.txt Honestly, this question was tricky, since there is a log entry showing that the attacker performed an iterative loop to traverse the file, which could be misunderstood as the attacker trying to save the content multiple times, so be careful.

6. Were any files deleted?
Using a little filter with strings like "Recipe" or "Recipe.tx" it is possible to see a "Remove-Item" command in the logs.

Command:
Remove-Item -Path .\Recipe.txt7. was the original "recipe" file deleted?
No, just recipe.txt was deleted.
8. What is the Event ID of the log that shows the actual command line used to delete the file?
When a command is executed using powershell, at least 3 events are triggered that detail the process performed by the system:
Event id 4104: Powershell load module
Event id 4105: Starting powershell command
Event id 4103: Execution itself, detailed command.

In this case, event 4104 is the correct answer of the question (block script creation).
9. Is the secret ingredient compromised (yes/no)?
As we see in some of the images, the content of the recipe was change in order to modify the secret ingredient, so the attacker changed honey for fish oil.
10. What is the secret ingredient?
The Honey :)
Some final words
Although the event gave you plenty of time to solve all the challenges, there were some external factors in my personal life that did not allow me to dedicate 100% of my free time to this competition. Even so, I am very happy with the result and I hope to participate again next year. Greetings and good year to all.